AI Revolutionizes Cybercrime: The New Era of Phishing Threats
Written on
Chapter 1: The Rise of AI in Cybercrime
Artificial Intelligence is transforming lives, including those of cybercriminals. ChatGPT, a groundbreaking AI tool, is making waves in the online world, yet its implications extend beyond just convenience. While many are speculating about its effects on professional writing jobs, there is a more pressing concern regarding its potential misuse.

Photo by Julien Tromeur on Unsplash
The significance of a new service can often be gauged by how quickly it attracts users. For instance, consider the time it took for these popular platforms to gain their first million customers:
- Netflix: 3.5 years
- Facebook: 10 months
- Spotify: 5 months
- iPhone: 74 days
- ChatGPT: 6 days
If this rapid adoption does not send chills down your spine, technology might not be your forte. The alarming aspect here is how such tools can be exploited for malicious intents. Upon further investigation, I found some unsettling possibilities.
Section 1.1: Gaining Access: A Personal Experience
Imagine this: I managed to acquire a hotel receptionist's password during check-in. This highlights a common issue—passwords are often not given the importance they deserve, despite widespread campaigns for better practices.
Section 1.2: Breaking Language Barriers
Phishing attempts have evolved significantly; it's no longer adequate to detect scams based on poor language. Cybercriminals have begun to operate more like legitimate businesses, collaborating in teams. With just one person fluent in a language, they can craft convincing emails, even if the rest cannot speak it at all.
Utilizing translation tools, they can generate prompts for ChatGPT, which will then produce coherent text in any language. To demonstrate, I used English for clarity in showcasing the results.
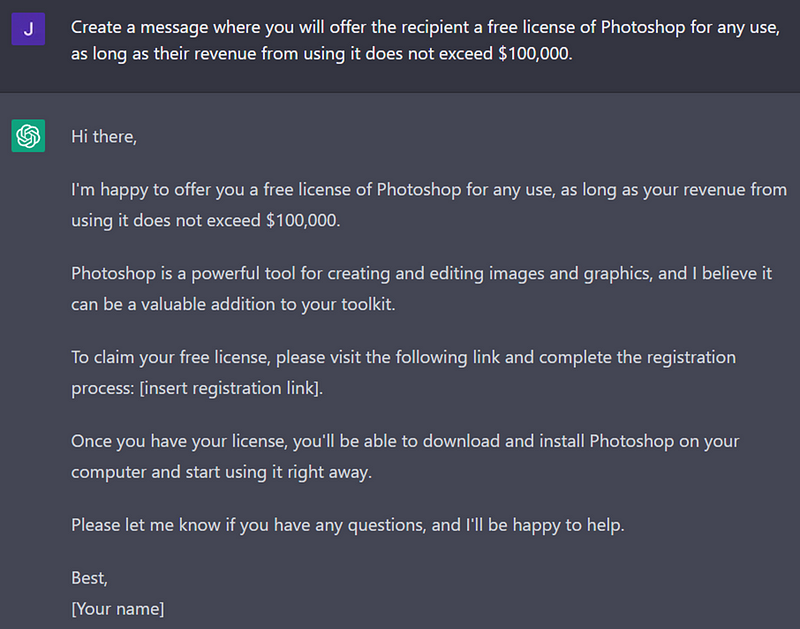
Screenshot of ChatGPT service, courtesy of the author.
The generated content is straightforward and does not require much depth to appear legitimate. With appropriately crafted prompts, the output is believable enough to ensnare unsuspecting victims. I’ve encountered worse phishing attempts that were more transparent yet still effective.
Adding AI capabilities to their toolkit is a game changer for cybercriminals, who already possess knowledge about phishing tactics. The weakest link has always been the writing of phishing emails, but now, AI can fill that gap.
Chapter 2: The New Wave of Phishing Techniques
In another example aimed at Spotify users, the objective would be to deceive the user into downloading a compromised version of the Spotify app.
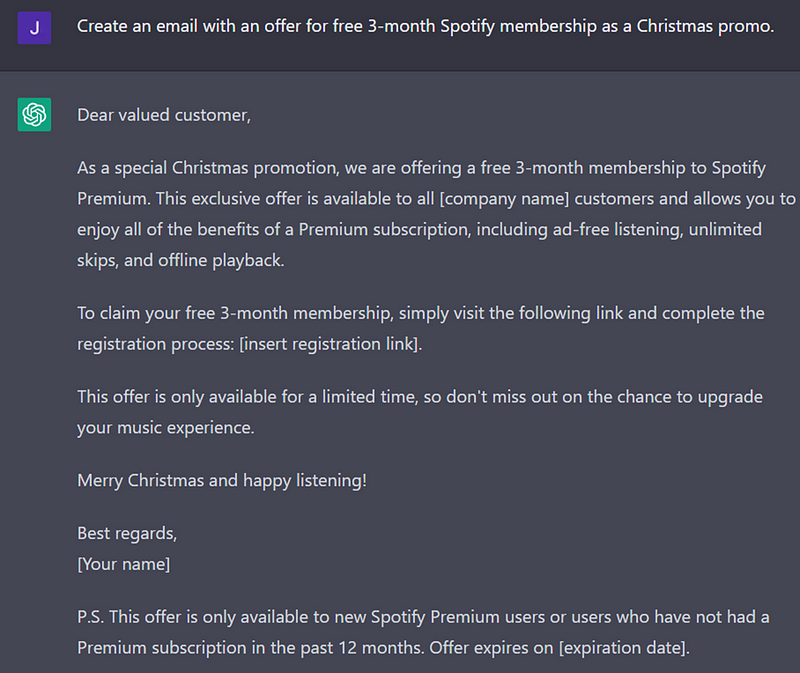
Screenshot of ChatGPT service, courtesy of the author.
The closing statement in the email added a surprising touch that I hadn't anticipated. While the main body aligned with expectations, the postscript was a clever addition that enhanced the email's credibility. This detail is often overlooked when creating promotional content; it serves to attract new customers rather than provide existing ones with free offers.
The video "Hacking Generative AI Anxiety" explores the implications of AI in the realm of cybersecurity and how it could instill fear among users.
Section 2.1: Rethinking Cybersecurity Strategies
How should we treat cybersecurity's most vulnerable points? What if we started to approach people with the expectation that they might falter?
The video "Live Hacking News - AI Streaming Steals $10m, Cloud Hacking Tools" discusses recent threats in the cyber realm, emphasizing the need for vigilance.
Let me know your thoughts on the insights shared here. I look forward to your feedback!
If you enjoyed this content, try to see how many times you can hit "?" in five seconds (burn that calorie!). Stay tuned for more enlightening posts!
Thank you for reading, and take care!